How a virus has wiped out 2009’s Modern Warfare 2 as Activision scrambles to get it fixed
 Activision/Infinity Ward/The National Archives (UK)
Activision/Infinity Ward/The National Archives (UK)Call of Duty: Modern Warfare 2 (2009) has had its servers shut down on Steam after a worm virus began to infect users.
After a revival of the old, original Modern Warfare 2 — since the player base has been complaining about the new Modern Warfare 2 — Activision has had to pull the plug on its servers. A worm virus had infected the servers and subsequently posed a huge risk to the reemerging player base.
In a vague tweet, Call of Duty’s official update Twitter account alerted players that they’d pulled the servers down due to “reports of an issue”. Since then, the game has remained down on PC.
Modern Warfare 2 was originally released in 2009 and has become notorious for the various hacks and attacks on players over the years.
What is a worm virus?
A worm is a malicious piece of software that can replicate and infect multiple systems from a single point of origin. Once started, it can be quite hard to stop if not nipped in the bud immediately.
Malware researchers discover Modern Warfare 2 server virus
First highlighted by the founder of VirusTotal, Bernardo Quintero, the worm that took down the servers was discovered on July 24. A prior version, found on July 18, came bundled with assumed beta files that weren’t supposed to be discovered.
These files revealed that the hacker at the source of the worm was working in a folder called “1337 Call of Duty.”
We approached Quintero for comment but received nothing back at the time of writing. However, Quintero did map out how the virus operates in a tweet. While a little messy, the graph details how it pings the information back and forth between Modern Warfare 2’s servers and the endpoint, the hacker.
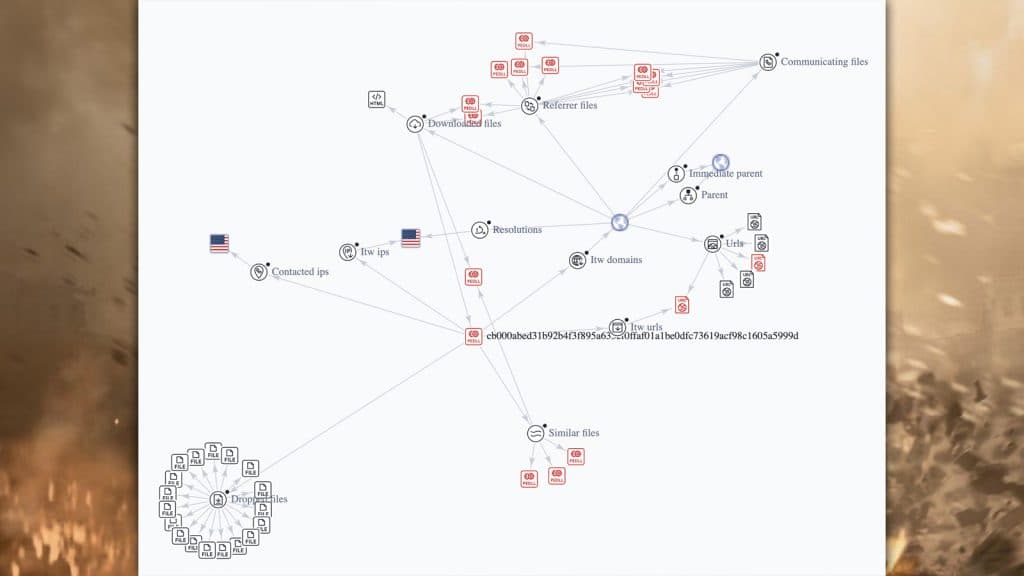 Bernardo Quintero
Bernardo QuinteroMalware research group VX-Underground breaks down MW2 virus
Instead, we contacted VX-Underground, a malware research group that hosts an array of viruses for research purposes. We came into contact with them after we were told that Privacy Affairs had tabs on them via Telegram.
VX-Underground usually focuses on much bigger threats, but the combination of nostalgia and niche victims brought it to their attention. We spoke to the person who leads the group:
“I know a lot of researchers (myself included) who don’t really game, but Modern Warfare 2 & 3, Halo 3, and Gears of War were peak high school gaming stuff, so this is kind of nostalgic.”

However, VX-Underground remains a little confused about the choice of audience. Modern Warfare 2’s revival might have gone viral in the right circles, but it’s still a drop in the water for targets:
“We typically look at malware that is targetting a widespread audience or is big game hunting ([for example] large corporations, governments, etc.). This particular worm, or strain of malware, is unique because it is targeting gamers.
“Gamers typically aren’t “good targets” because generally speaking threat actors (or serious ones…) look for big money. Targeting individual home users, normal nerds playing Call of Duty isn’t going to yield big money. However, despite this, it’s still pretty cool.”
How the Modern Warfare 2 server virus works

The small adoration shown is more to do with the way the worm was implemented. Essentially, the virus exploits key parts of Modern Warfare 2’s file structure and how the game loads up files. VX-Underground says it’s a common method to exploit “DLL sideloading”:
“Windows has a library called dsound.dll, which is used for sound… It’s a totally benign library, it is used all the time.
“However, in [Modern Warfare 2] 2009, the programmers made a slight mistake (among others…).
“When the game tries to load dsound.dll it is supposed to specify the full to the library.”
Typically this is found in the system files of the operating system, but what’s been uncovered is that if you place the DLL file into Modern Warfare 2’s directory, it’ll replace the searching of Windows system files and default to that.
After it loads up the infected DLL, the game has no way to properly parse whether or not it is fake. It’ll just continue as normal.
“Then when Modern Warfare 2 tries to use the function “directsoundcreate,” the malware does it [instead], then starts the worm.”
We were shown annotated screenshots of the code, and VX-Underground points out that it does create a legitimate call for the file, but then immediately “doing stuff it’s not supposed to”.
Once the worm is loose within the game, it connects to other players and repeats the process. All it takes is to be in the same lobby as an infected user and you have another 17 infected players.
MW2 hacker leaves traces back to their digital doorstep
As it caught the attention of infosec researchers, the worm was deconstructed and discovered to be riddled with mistakes. Some of these could easily lead Activision straight to the doorstep of the hacker.
“Older versions would try to download from a website. He also left “get cucked by shiny”.
“They bought [the domain] from Name.com, so they better hope law enforcement (or Activision) doesn’t pressure Name.com into giving information on who bought it.”
VX-Underground found that the hacker’s ability or knowledge to hide “isn’t very good”:
“[They] used United States-based servers, and United States registrants. He [also] left programming artifacts.”
Using WhoIs, a domain registration tracker, which will share any personal information you’ve not opted to keep private while signing up for your domain. The website in question was made 119 days ago and appears to be based out of Ohio.
VX-Underground also ruminated on whether or not the hacker intended for the worm to get as big as it did. Originally reported by TechCrunch, it appears his target had an unintended effect. As mentioned before, Modern Warfare 2 was incredibly popular when a lot of current researchers and infosec people were teenagers or young adults.
Activision confirms no timeline for bringing back MW2 2009 online

We reached out to Activision for comment, and their public relations team confirmed that there’s “no definitive timeline at the moment” for bringing the servers back up:
“The issue is currently being worked on, and we hope to have [it] rectified ASAP so PC players can get back to enjoying the MWII (2009) experience on Steam again.”
It’s also unknown how many people were infected.